My Australian mate, Mal Cowan, steps into the breech when his good friend gets infected with one of the most difficult to remove pieces of malware currently ripping up the Internet – ransomware. Follow Mal, in this guest writer article, as he spins up his skill set and puts the hammer to a ransomware payload cybercrime.
 Recently, I received a frantic call from a good friend. He informed me that when he booted his computer, there was a message supposedly from Australian Law Enforcement, stating that his PC had been involved in illegal activity and, distributing pornographic material.
Recently, I received a frantic call from a good friend. He informed me that when he booted his computer, there was a message supposedly from Australian Law Enforcement, stating that his PC had been involved in illegal activity and, distributing pornographic material.
Freak-out time – The malware had taken a photo of him via his webcam and placed it in the top middle of the Law Enforcement notice.
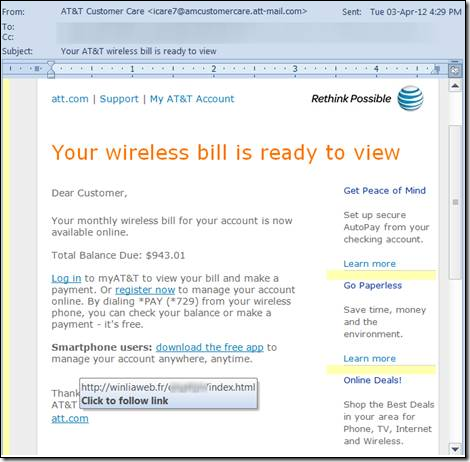
Note: This scam is not restricted to Australia. The graphic below provides ample evidence that this type of ransomware is a global issue.

Graphic courtesy of F-Secure.
Immediately, I knew what this program was – Ransomware. Tech and blog sites have been full of news of this scourge in the past few months.
At first look, there was a full screen message – complete with an official looking logo from the Australian Federal Police. The computer’s IP address had been logged, and there was indeed a photo of my friend, along with the messages outlined above.
The clincher? The message stated that he had to pay a fine to unlock his computer.
First, I tried to start Task Manager to stop the malware process. That did not work – it simply would not load. The computer was well and truly locked.
Next, I tried to restart the computer in Safe Mode. No luck. The message appeared again. Still frozen.
Then, I inserted Kaspersky Rescue Disk (a fantastic Linux based recovery disk made for just this type of situation), and restarted the computer.
Selecting boot options before Windows started, I loaded Kaspersky and updated the malware database via the Internet. The wonderful thing about Kaspersky is, it scans the infected machine without Windows running, so anything nasty cannot hide.
After a three hour scan, Kaspersky came up with 50 Trojan detections (one of the biggest I have ever seen). It was able to eliminate all but one of them.
I crossed my fingers and restarted Windows. Instead of the message, there was just a big white screen – still locked. Kaspersky had obviously made a dent, but I needed something more.
Before leaving for my friends house, I had loaded up a USB stick with Hitman Pro Kickstart. Hitman Pro is a wonderful true cloud antivirus scanner using multiple AV engines, with an excellent detection rate.
Recently, it also added a feature in which one can create a bootable USB stick that can bypasses the infected boot process. The catch is – this must be done on an uninfected machine (which is why I used my personal computer to create it).
I inserted the USB stick into the slot, restarted the machine, and went to boot options (the F12 key on the infected machine) and selected “Boot from USB”.
Hitman Pro Kickstart came through. It booted straight into the Windows environment without a hitch, and then proceeded to run a scan (an Internet connection is required). I was a bit dismayed when the scan came back clean, as I knew Kaspersky had not been able to eliminate one threat.
But now, I was past the ransomware Trojan and able to start other antimalware applications. Malwarebytes was next. I updated it and proceeded to run a full scan. Bingo. It nailed a few more Trojans that had got past Kaspersky and Hitman Pro, and after deleting these nasties and rebooting the computer normally again, a further scan with Hitman Pro, Malwarebytes and AVG, the computer came up clean.
The point of my story really is quite simple. NOBODY can rely on one antivirus/antimalware application to catch all malware. The ransomware obviously got past the onboard, realtime antivirus (which was not AVG, I installed that afterwards). Kaspersky detected most of the infections, Hitman Pro helped me boot into the Windows environment, and Malwarebytes cleaned up the rest. AVG came up with a clean scan after I uninstalled the old antivirus.
How did my friend get infected? Who knows. There are so many exploits that this Trojan could have used that I don’t have a clue. The computer is a family machine, used mostly by children for online games and such.
Just visiting a family friendly site can get your computer infected these days. It could have been worse. It might have been an infection that actually encrypted the contents of the whole computer. That’s a nightmare I am glad I didn’t have to deal with.
Thanks Mal. ![]()