It’s often said that “no good deed goes unpunished”. Generally, this statement means that one can attempt to be helpful to others, and despite good intentions, end up paying an unexpected price.
That seems to be the case in Zemana’s good deed, in providing a free license for their superb security application; AntiLogger.
Over the course of the last few days, in conjunction with Zemana, Tech Thoughts, has been offering a free license for AntiLogger and the response has been very gratifying. For more information on this offer please read “Free Licenses for Zemana AntiLogger – 3 Days Only”, on this site.
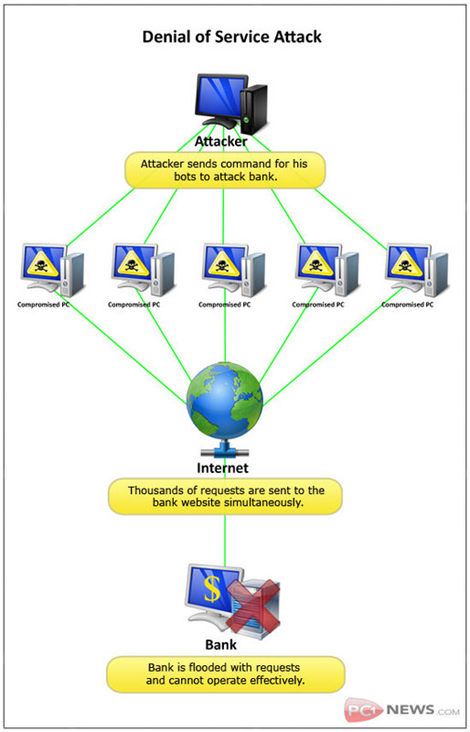
Unfortunately, cybercriminals, who as we know are driven by opportunity, obviously saw in this free license giveaway, an opportunity to be disruptive by launching a distributed denial-of-service attack, driven by a bot network, against the Zemana license server.
If you’re unfamiliar this this type of attack, Wikipedia explains it, in part, as follows:
A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer resource unavailable to its intended users. One common method of attack involves saturating the target (victim) machine with external communications requests, such that it cannot respond to legitimate traffic, or responds so slowly as to be rendered effectively unavailable. In general terms, DoS attacks are implemented by either forcing the targeted computer(s) to reset, or consuming its resources so that it can no longer provide its intended service or obstructing the communication media between the intended users and the victim so that they can no longer communicate adequately.
There are very sensible business reasons why a company, such as Zemana, gets involved in this type of promotion, but at the end of the day, it’s the individual who receives a free license who benefits immediately.
While this attack has been extremely disruptive, and very inconvenient for those readers who choose to take advantage of Zemana’s generous offer, in a real sense this attack emphasizes the level of cybercriminal activity on the Internet, and the lengths to which these Neolithic idiots will go to threaten our enjoyment of the Net.
Inadvertently, those responsible for this attack have proven how important it is to ensure, that you as an Internet user are adequately protected against cybercriminal activity. The very definition of irony.
If you found this article useful, why not subscribe to this Blog via RSS, or email? It’s easy; just click on this link and you’ll never miss another Tech Thoughts article.


Pingback: Free Licenses for Zemana AntiLogger – 3 Days Only « Bill Mullins’ Weblog – Tech Thoughts
Hey Bill,
Zemana AntiLogger Server Attacked by Bots
What action would you (take or) recommend in the event of a “DoS” assault.
They appear to be happening with increased frequency?
Thanks
Hey Zbob,
DoS attacks are virtually as old as the Net itself, and there’s no doubt that we will have to continue to deal with this issue. But, we are getting better at recognizing the early symptoms of these attacks – and that’s the key to defeating them.
There are now a host of network appliances (including specially hardened Firewalls), supplemented by software applications, that are specifically designed to defeat a Dos attack in the early stages.
Unfortunately, cybercriminals are highly creative and so DoS attacks will continue. Part of the problem of course is, many companies do not take advantage of enterprise solutions until they have suffered the consequences of a DoS attack.
While not directly related; take a look at the number of companies that are still using IE 6 – makes you want to just shake your head.
BTW, the Internet has some great resources on DoS attacks – just do a Google search if you’re interested in this complex issue.
Bill
The Internet is not such a fun place at times , it seems we always have to keep our guard up
Hey Greg,
The Internet is a reflection of the human condition. There are good people, there are are bad people, and there are worse people. Cybercriminals, very obviously, fall into the latter category and we will never be rid of them.
Your comment “it seems we always have to keep our guard up”, is an unfortunate reality. Very tiresome – but necessary.
Bill
Bill,
I don’t agree with torture, but scum who do this sort of thing should be flogged in public!
Liam
Hi Liam,
Seems a little harsh, but…………
Bill
Hey Bill,
My bad; I should have been more specific with my question. As in the case of Zemana’s server being attacked. Is there any SOP defense to limit site crashing?
Thanks
Hey Zbob,
I could be here all day answering your question, since there are multiple and complex answers. I could write 10+ articles on this issue alone, but typical readers on this site, to this point, have shown little interest in the technology involved. I should point out, it is my practice to answer only those questions that have relevancy to a typical user. I’m sorry, but your question unfortunately, is outside the purview of this site.
The best answer to your questions can be found on Cisco’s site – Strategies to Protect Against Distributed Denial of Service (DDoS) Attacks, which I think will answer any questions you might have on this complex issue.
BTW, I cannot specifically discuss Zemana’s response to the attack on their server.
Bill
iam very sad to see such a good company as Zemana gets attacked by DoS. whats Zemana going to do in response on these attacks?
thank you Bill .
Hey Ahmed,
While I’m aware of the specific steps which Zemana took in dealing with this issue, I cannot discuss the particulars. The steps taken by Zemana, seem to be working – at least at the moment.
Bill
Hey Bill,
Thanks for the Cisco lead.
Zemana has “walked the walk” by their generous license giveaway.
It is time that we demand our elected officials put some teeth into internet crime law enforcement!
Hey Zbob,
Absolutely agree – we need a concerted effort by government to address this issue. Part of the problem, it seems to me is, the complexity of the technology is barely understood by those we have elected to protect us. So, they simply throw up there hands, and then offer us a bag full of excuses as to why the obstacles to cybercrime control cannot be overcome.
I hold no expectations that we’ll soon see any positive action on this issue. I’m familiar with all of the “can’t be done’s”.
Bill
Hi Bill,
I am totally shocked after hearing this news!It seems quite clear that cyber-criminals are hell-bent on commiting there detestable,vicious and heinous acts against all odds.Gone are days of total secure protection.I feel bad for Zemana and absolutely appreciate their generous giveaway of license’s to the masses.The people behind the DDOS should be condemned and severely punished.The Cyber-law authorities should get it acts together before more incidents like this affect common good-willed people and companies.
Hey Kingpin,
Ah, but there’s the problem “the Cyber-law authorities should get it acts together”. There is no common consensus on cybercrime, much less any regulatory body, or enforcement agency, that can deal with this issue. Unfortunately, we’re on our own when it comes to protection. Both individual users, and enterprise alike. Sort of like a sinking ship – every man for himself. Sad, really.
Bill
Hi Bill,
Thanks for replying!Yes now I clearly understand by what you said.Well unfortunately even the best security have some loopholes and cyber-criminals just need one of those to exploit us and not to mention new types of attacks,clearly these clever scum’s are ahead of the game and taking advantage of every single vulnerability.Sad but true.
Hi Bill,
is it possible that the attackers are the same persons who are asking for free keys?
They probably do not know all those requests can actually overload a server.
Hey Leofelix,
The short answer, in this particular case, is no. The number of requests are well within acceptable limits.
Server software can be set to respond to an unusual number of requests from the same, or multiple locations, and filter those requests appropriately. In this instance though, the server was being bombarded by up to 100,000 requests PER SECOND. Six million requests per minute!
Bill
Hey Bill,
Your comment on IE6 is interesting, personally, I don’t use IE of any version whatsover anymore, I don’t trust it. It only stays on my system as some other programs I use need it installed, otherwise it would be gone for good.
Cheers
Hey Mal,
Here’s an item from my today’s Tech Net Daily Net News column – *Google phasing out support for IE6 * � Starting March 1st, Internet Explorer users must be running at least version 7 of the browser in order to properly use Google Docs and Google Sites.
You’re right in not trusting IE 6. Unfortunately, the large number of companies, and government agencies, that continue to use it is very disappointing. Recently, I did a piece on this very issue – Who�s Still Using IE 6? � Some Outrageous Surprises .
Bill
Zemana creation very good product-program.Reaction? Attack.Unbelievable.
Robert,
You may be right. It does seem as if there is a message here.
Bill
I say we bring back tar and feathering :^) Its a shame a few bad eggs try to mess it up for everyone. Though I must say I love Zemana AntiLogger and I will buy from them from now on.
Hey RoseD1st (Rose the first?),
I like your solution – just the right “touch”. It seems to have worked in by-gone days, so ………………
Zemana has handled a very difficult situation in a graceful, courteous, competent and professional manner. This is the type of company that I personally like to do do business with, and better yet, in my view, AntiLogger is in a class by itself.
Good to hear you will continue to do business with Zemana.
Best,
Bill
Flashback: 4may2001
Guru SteveGibson wrote a real nailbiter,
‘The Strange Tale of Denial of Service Attacks Against GRC.Com’ Alas,it seems that story has dropped off the edge of the internet.
But the following are decent substitutes:
http://www.princeton.edu/~rblee/ELE572F02presentations/DDoS.ppt
Click to access grc_attacks.pdf
cheers,
dar
Hey Dar,
Thanks for this – a great learning resource for those who are interested in DoS.
Much appreciated.
Best,
Bill
Such a sad news… Your right.. Good deeds never go without paying a unexpected price..
Hope, they may get it solved and the culprits be punished…
Hey Ranjan,
Zemana did a great job in solving this issue as quickly as possible. Unfortunately, I doubt if the culprits will ever be caught.
Thanks for visiting.
Bill
Very sad news to here.. this was unexpected 😦
Thanks Bill and Zemana
I tested it with my Norton and Online Armor++, no conflicts, works fine. Nuff said
Cheers
Bye
Thanks for your report Ashwin – much appreciated.
Bill
No, no.. Let me thank you Bill…
Only by your help, i was able to get a license of Zemana..
I read your blog as soon as it arrives in my mailbox..
Keep it up..
Thanks Ranjan.
Best,
Bill
Not true DoS attack Bill, it is Pushdo junk SSL attack.
#1 visible target is AntiVirus Australia, company who represent of Eset + Zemana.
http://www.eset.com.au is attack 1/30, again 1/31.
http://www.zemana.com.au is attack 1/31.
http://www.zemana.com is attack 1/31, 4hrs after.
Savik,
You’re not quite correct *in this instance*. While it’s true that Pushdo is active – see The Hand of *Pushdo* behind CIA, PayPal *SSL* assault, the attack on Zemana used an entirely different attack vector.
Bill
Pingback: uberVU - social comments
Sorry Bill, my bad. I am only half-correct. :o)
eset.com.au is attack of the Pushbot. I mistaken am concluding zemana.com.au is same Pushdot attack because it is same time, same Company.
So, it is you think 2 attacks by 2 Vandals?
Next time I shut up to check fact 1st before I post. :o)
teşekkürler. başarılarınızın devamını diliyorum
Translation: thanks. I wish continued success
Thank you, fly flion.
Bill